As the world continues to digitize, the number of internet users is intensifying at an explosive rate. According to Statista, almost 4.57 billion people were active internet users as of April 2020; that’s 59% of the global population. Cybersecurity Venture predicts that 90% of the human population will be online by 2030.
Today, the internet is part of our everyday life. Corporations use it to communicate with customers and sell products and services. Government agencies utilize it to increase the efficiency of public services; individuals use the internet to socialize and communicate with others anywhere on earth, read the news, and conduct business from home.
The massive adoption of internet technologies has led to an equal increase in cybercrime. Cybersecurity Venture gives us an in-depth look at the future growth of cybercrime, estimating that cybercrime damages will reach $6 trillion by 2021.
Governments and corporations from all industries are spending billions of dollars annually on purchasing security solutions to stop and mitigate cyberattacks, while government leaders and management in private organizations still think security is merely a technological problem.
The real problem in any security chain, however, is human error. Educating yourself and your company about cybersecurity defense techniques is the key to stopping future cyberattacks.
Several different attack vectors, or methods, are deployed by cybercriminals to penetrate target systems and networks. The most devastating attack bypasses any security solution by exploiting humans to gain unauthorized access. This cyberattack is known as a social engineering attack and categorized as an internet and phone-based phishing attack.
What is a Phishing Attack?
Phishing is a type of cybercrime where an attacker pretends to be a legitimate entity, like an official public organization and tries to acquire sensitive information –such as login credentials, credit card info, and personal information- from victims.
The ultimate goal is to gain unauthorized access to target accounts, such as online banking, or to collect intelligence to help launch further attacks against the target of interest.
How Does Phishing Work?
Phishing attacks can be initiated through the internet or by phone, however, attackers prefer using the internet because it makes it easier to conceal their traces. When launching phishing attacks online, attackers use social media messages or malicious advertisements to hunt for victims; nevertheless, email remains the most popular method.
In email phishing, an attacker sends an email pretending to be a legitimate organization such as a bank, social media networking site, cloud storage provider, or Internet Service Provider (ISP). It’s made to look like a legitimate email asking the victim to open an attached file containing malicious software.
Other phishing attacks may manipulate you into clicking on a link within an email, which initiates an unwanted action, such as updating account info.
General Characteristics of Phishing Emails
Different factors distinguish phishing emails from other ordinary emails. Here are five tips for identifying hazardous activity.
1. Phishing emails use threatening language to convince the victim to act without thinking. See Figure 1 for an example of a phishing email that asks the victim to respond promptly before their email account gets deactivated.
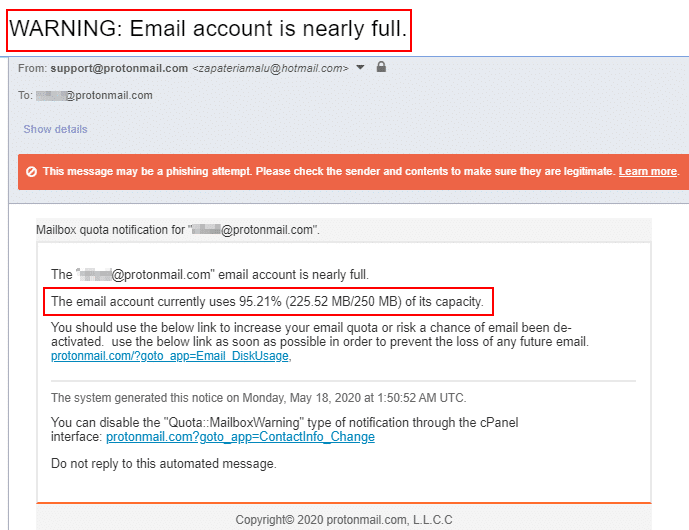
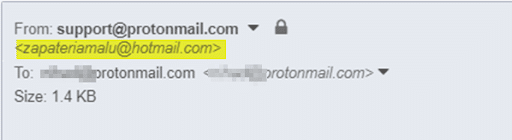
2. Check the sender’s name and email address. In Figure 1, the sender pretended to be from support@protonmail.com; however, the sender’s real email was zapateriamalu@hotmail.com (see Figure 2). Suspicious or mismatched sender information is the first clear sign of a phishing email.
Keep in mind that an email service provider like ProtonMail.com will not send emails using an account from another email provider, hotmail.com.
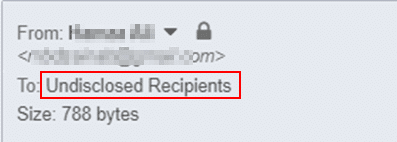
3. Next, investigate the “To” field in a suspicious email. In Figure 3, we notice that the email is sent to “Undisclosed Recipients.” This means the email is being sent in bulk to many recipients at once without displaying their addresses.
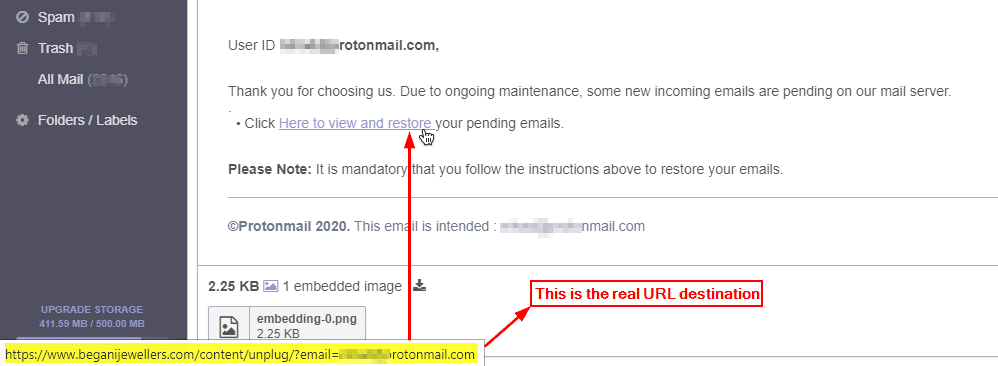
4. After that, investigate the hyperlinks included within the suspicious email message. It’s easy to do—hover your mouse cursor over the hyperlink and see the real destination address (see Figure 4).
5. Finally, investigate email attachments. Although it is common to receive emails with PDF, MS Word, or Excel files attached, you should be very careful before opening such file types and ensure that you know the sender well. If the attached file is executable, meaning that a computer can run it, do not open or execute it.
Phishing emails are often sent randomly to various recipients hoping that a small percentage of them will overlook the signs and execute an attachment or mishandle sensitive information. Another type of phishing is called spear phishing, which is more targeted against a single individual.
What is Spear Phishing?
Spear phishing is a subtype of phishing attacks where intruders gather information about a specific individual to craft a customized email message. The goal is to gain the target’s trust and bypass all security controls to convince the target to execute an attachment or mishandle sensitive information that can help attackers gain entry into the IT system and network.
Successful spear phishing attacks require cybercriminals to collect intelligence about their target by utilizing all publicly available information such as social media platforms, corporate profiles, people search engines, and much more.
This type of intelligence collection is named Open Source Intelligence (OSINT).
6 Countermeasures Against Phishing and Spear Phishing Attacks
There is no 100% foolproof solution to stop phishing attacks; however, following these simple protective steps can prevent sensitive information from being compromised.
- 1. Do not publish personal information online. Spear phishing depends on knowing some personal information about the target to customize the attack.
- 2. Do not click hyperlinks within suspicious emails; always hover over the URL to reveal the exact destination.
- 3. Do not open attachments from unrecognized senders. If the attachment contains an executable file, do not run it. If the attachment contains MS Office files, do not enable macros when launching such files to avoid installing malware on your computer if the file is malicious.
- 4. Do not access untrusted websites and never click on pop-up advertisements.
- 5. If you feel suspicious about a particular email, try to communicate directly with the sender via phone or internet messaging applications.
- 6. Install an antivirus solution with phishing protection, and make sure your operating system and installed applications are all current. An antivirus solution is your final defense if you execute a malicious attachment within a phishing email inadvertently.
Human error is still a concern in any cybersecurity defense plan. Installing security solutions on endpoints and perimeter devices is very important; however, without recognizing phishing emails and understanding the security risks associated with such emails, your defense plan will remain highly subject to failure.
There are millions of cybersecurity jobs waiting to be filled and countless organizations in need of cybersecurity professionals who know how to protect networks and data from malicious cybercriminals. Now is the time to start your career with the University of Miami Cybersecurity Bootcamp.
With industry experts leading each course and a career support team ready to help you land the job of your dreams, you’ll be ready to face and eliminate phishing attacks and so much more in less than a year. Take the first step in your new career and fill out the form below or call us at (305) 425-1151.



