The term “cloud computing” has been around for many years and since then, there has been a mass adoption of cloud technology. Today, it’s safe to say that a majority of people are moving to the cloud, even though they may not realize it. Most people have smartphones, laptops, and tablets, bringing them even closer to the cloud.
If you are using an Apple/IOS device, then you are using Apple’s proprietary Cloud. Almost every company has embraced the cloud in one way or another, with some companies running 100% of their infrastructure in the Cloud.
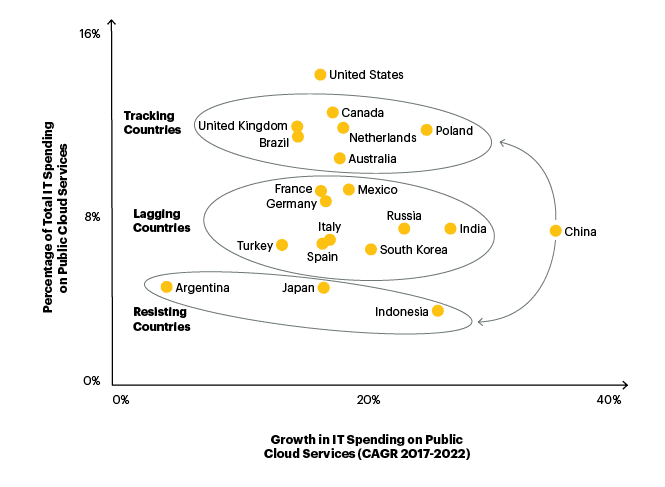
According to Gartner research on cloud spend and growth per location, many countries are quickly embracing this new technology. LogicMonitor’s Future of the Cloud study predicts that 83% of enterprise workloads will be in the cloud by 2020.
What is “The Cloud”?
Cloud computing is a series of computers, networking, and storage devices that allow companies like Microsoft Azure to provide a seamlessly integrated network of backend (and frontend) services for the best user experience.
For example, data we consume or use every day, like documents, pictures, and videos, are saved or accessed over the internet, instead of via physical hardware such as computer hard drives or mobile devices. You might be familiar with Microsoft OneDrive, Google Drive, Google Photos, iCloud, Samsung Cloud, and other services for saving your valuable data; when you use these, you are storing and accessing data using the cloud.
How Does Cloud Storage Work?
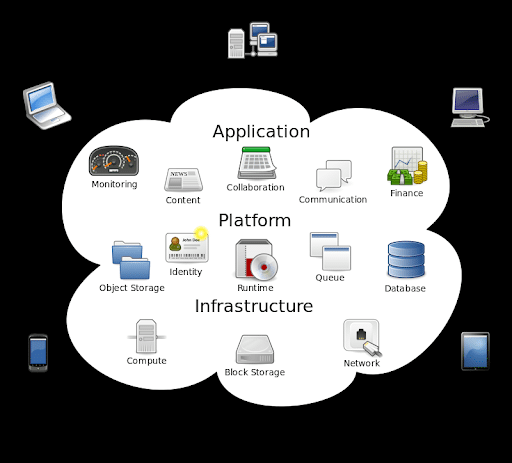
Cloud storage utilizes off-site servers to store data. The data is stored on various servers distributed in the network. In other words, users connect to the cloud using the internet, and then the cloud server they connect with forwards the data to a pool of physical servers positioned in one or more remote data hubs.
As part of an optional paid service, cloud providers save the same data on various servers as a backup. This means, if a server is down for support or undergoes an outage, users can still access their data without interruption.
Think of cloud computing as a supplemental resource for computing memory, power, and space. Instead of saving files on physical hardware, the cloud offers a way to store data and run applications on off-site servers.
Benefits of Using Cloud Computing
Cloud usage can significantly decrease IT and maintenance costs accrued from having to buy, install, support, and update physical hardware. As mentioned before, cloud computing is also scalable, enabling IT staff to distribute or deliver the proper amount of resources, from storage to bandwidth, efficiently and in a short amount of time.
Ultimately, cloud computing services delivered via a global chain of reliable data centers can decrease wait times for application and data access.
Here are some additional benefits of cloud storage:
- Accessibility. As long as you have internet access, you can access your files from anywhere in the world at any time.
- Cost-efficiency. You don’t need to purchase additional hard drives or devices for more storage. The cloud grows with you as you grow.
- Security. Cloud storage implements various security methods such as authentication, access control, and encryption. This is optional; none of the “Big Three” – Amazon Web Services (AWS), Microsoft Azure and Google Cloud – provide this service automatically.
- Automation. Software-based solutions automate the installation, configuration, and administration of cloud computing services to lessen manual works of monotonous tasks.
- Easy file sharing. Securely share files with others via email or a link.
- Multiple users.
- Disaster recovery. As files are backed up on multiple servers, accessibility is possible even if one server is out of service. This feature is optional and requires additional set up from your provider.
- Synchronization.
Types of Cloud Computing
Now that you know the basics of cloud computing, you’ll notice there are several ways to use cloud resources: public, private, and hybrid cloud. All three deployment methods offer similar advantages, like cost-effectiveness, administration capabilities, security, and scalability—but which method you need depends on your requirements. Let’s take a look at each one in detail.
- Public Cloud: The public cloud is the most popular model of cloud computing. In this model, servers and storage are managed by a third-party cloud service provider and distributed over the Internet. Users access services and maintain their account via a web browser. Public cloud deployments are often used for email, online applications, storage, and development environments.Individuals and small and medium-sized businesses usually use this option. Microsoft Azure and Google Cloud are examples of a public cloud.
- Private Cloud: In contrast to a public cloud, a private cloud is offered over a private internal network and is utilized by select companies or users. In a private cloud, all cloud computing services are hosted privately. The company normally manages the administration and maintenance of the private cloud. In general, cloud computing enables companies to move data storage, and other services away from on-premises servers and onto remote servers that employees or clients can access via the Internet. An organization that wants to utilize cloud computing services may pick between a private cloud (where cloud services are private to the company) and a public cloud (where cloud services are maintained and controlled by a provider).
- Hybrid Cloud: The hybrid cloud model combines private clouds with public clouds so companies can get the best of both worlds. In a hybrid cloud, data can migrate between private and public clouds for more adaptability. For example, you can utilize the public cloud for less-confidential communications while using the private cloud for highly-classified files like business reports.
Tips for Securing Your Cloud
Yes, your files, information, and data are more secure in the cloud than your hard drive, but using cloud services means your data is eventually in the hands of a third party. Access to information and files requires – sometimes multiple levels of – authentication. If you’re willing to save data on the cloud, follow these best practices to keep your data secure:
- Use strong passwords and 2 Factor Authentication (2FA): Always use different passwords when storing your data on the cloud and secure your login with two-factor authentication.
- Backup your files in various accounts: Never put all your files and data in one account. Always back up all the files in different cloud accounts.
- Practice clever browsing: If you’re using the cloud on a local or public computer, be sure to log out and never save passwords to the browser.
- Use encryption services: For more comprehensive privacy, always go for cloud storage that allows data encryption. This adds a layer of security as the data or files will have to be decrypted to obtain access. This arrangement secures the data even from cloud providers.
- Use a trusted cloud provider: A sign of a serious provider is the variety of security capabilities and certifications they possess. Any reputable provider will make these openly available. For instance, all major cloud providers like Google Cloud, Amazon Web Services, and Azure allow users to check and verify their safety compliance.
- Be careful about your online presence: Never use open and unsecured Wi-Fi networks to log in to your cloud account. These connections are often unencrypted and your activity can be ‘sniffed‘ by a hacker on the same network. Hackers use “sniffing” tools as a way to wiretap information from your shared network, this includes login data for your cloud account.
Uses of Cloud Computing

Businesses of all sizes have recognized cloud computing’s cost minimization, greater compliance capabilities, and flexibility. Here are a few examples in which cloud computing is applied to maximize business goals.
- Infrastructure as a service (IaaS), Software as a Service (SaaS), Platform as a service (PaaS): IaaS includes current infrastructure on a pay-per-use plan that saves the cost of acquiring, running, and managing IT infrastructure. There are also situations where companies move to PaaS for identical reasons with the added bonus of a ready-to-use platform. SaaS has revolutionized how teams communicate and operate. Google Docs, Microsoft Office 365, and Quicken Loans are prime examples of businesses leveraging cloud technology.
- Disaster recovery: Using cloud-based solutions allows businesses to face security breaches or human disasters with more peace of mind. For example, if a hurricane affects your physical office location, you can still access files and information from your cloud storage and operate as usual, for the most part.
Final Verdict
Migrating to the cloud can be a gamechanger for many businesses. It provides sufficient data space without dependence on hardware while offering scalability and agility. Still, as the cloud can be a public solution, it has its security risks. Building a cloud security ecosystem with multi-layered security, encryption, identity access management, and 24/7 monitoring is necessary. Hiring IT professionals with cloud security certifications is a crucial part of a business’s quality control and security efforts.
For those looking to work in cloud technology or cybersecurity, having well-known cloud security certifications shows employers that you’re ready to protect them against potential data breaches to their cloud environment.
Before you can take certifications, start your hands-on training with an immersive program led by industry experts. The University of Miami Cybersecurity Bootcamp helps individuals of all experience levels enter the cybersecurity field in less than a year. Get out of the clouds and into your new career with a certificate of completion in Cybersecurity. Fill out the form below to get in touch with our admissions team.



