Cybersecurity is a fascinating and growing area, covering many topics, from employee security awareness to critical infrastructure protection. One of the most important cybersecurity topics is the security of data and the person(s) and processes this data reflects.
The discipline of Operations Security (OPSEC) is a holistic and analytical approach to protecting critical information.

What is Operations Security?
The concept of Operations Security (OPSEC) originated in military circles to understand adversaries and protect secrets and operations. The OPSEC program developed by the United States, known as ’Purple Dragon’, was used during the Vietnam War to understand how adversaries were able to infiltrate military strategies. Purple Dragon used a technique called “thinking like the wolf” to discover that adversaries used aggregation of unclassified information released by the military to exploit operations.
Before Purple Dragon, however, a slogan perpetuated throughout the country during World War II in the 1940s, “Loose Lips Sink Ships.” This was meant to discourage careless talk that could have undermined war efforts. While this was not an official form of OPSEC, the function of the concept remains.
OPSEC, in military terms, is used to protect mission-critical information. That is, data, ideas, etc., in the wrong hands, could compromise a military operation. In a business context, the principles of OPSEC protect an organization against cybercriminal activity.
Why Data Needs Protection

An individual piece of data, say an IP address, may not be sensitive as it gives little exploitable information; however, the more sensitive the data becomes, the more exploitable it is (e.g., personal data such as name, Social Security Number, etc.) The more data a hacker can obtain, the likelihood of exploitation also increases. If you take multiple pieces of data and aggregate them together, they form a picture. This bigger picture gives cybercriminals enough information to commit crimes such as identity theft.
Cybercriminals use many techniques to exploit data for fraud purposes, including malware, phishing, vulnerabilities in software, and insecure configuration. OPSEC practitioners need to understand how data and threats are woven together.
The Five Steps in Operations Security
Operations Security (OPSEC) is a process involving five-steps:
Identify Critical Information
It all starts with knowing what data an organization has and how it is used. Sensitive data can be Personally Identifiable Information (PII), i.e., any information used to identify an individual. This could be a person’s name, Social Security Number, etc. Other sensitive data includes proprietary information, financial data, Intellectual Property (IP), etc. OPSEC begins by knowing the types of data used in an organization.
Identify the Threats
Cyber-threats come in many forms. Often these threats are specific to a specific type of company or data. ‘Threat actors’ can be state-sponsored, competitors, hacking groups, individuals, etc. This part of the process is about understanding how and why an organization is being targeted.
Hunting Vulnerabilities
Vulnerability hunting is typically done using automated tools and manual tests. Knowing how and where threats can turn to exploits is a critical step in the OPSEC process. This part of the process can be both challenging and exciting, using your skill and know-how to think like a hacker and work out where attacks could happen.
Setting Risk Levels
Assessment of risk levels is an essential part of managing Operations Security. Risk is always present in an enterprise, as such, risk mitigation is an essential part of the process of securing an organization. In a modern enterprise, there are vast amounts of data and associated threats. Without some form of risk level classification, an organization could easily become overwhelmed with protecting their data.
When applied, risk levels reflect the relative importance of the data and threat. For example, a high-risk level (e.g., administrator credentials or company IP) would require more aggressive countermeasures than a lower risk level, such as publicly accessible non-critical data.
Putting Countermeasures in Place
Countermeasures mitigate vulnerabilities based on the risk level. There is a balance between countermeasure cost, loss of critical data, and impact on operations. Countermeasures include technical and non-technical measures. Examples of countermeasures include encryption, ‘clean-desk’ policies, security awareness training, robust access control, cleaning whiteboards after meetings, etc.
Where mitigation involves creating strategies to minimize an inevitable attack, remediation destroys the threat altogether. Both mitigation and remediation are part of a healthy risk assessment, which helps to complete an organization’s threat intelligence. This, along with maintaining CIA (confidentiality, integrity, availability) are crucial to implementing robust countermeasures.

Common Operations Security Threats and Their Solutions
Some common threats and countermeasures in OPSEC are shown in the table below:
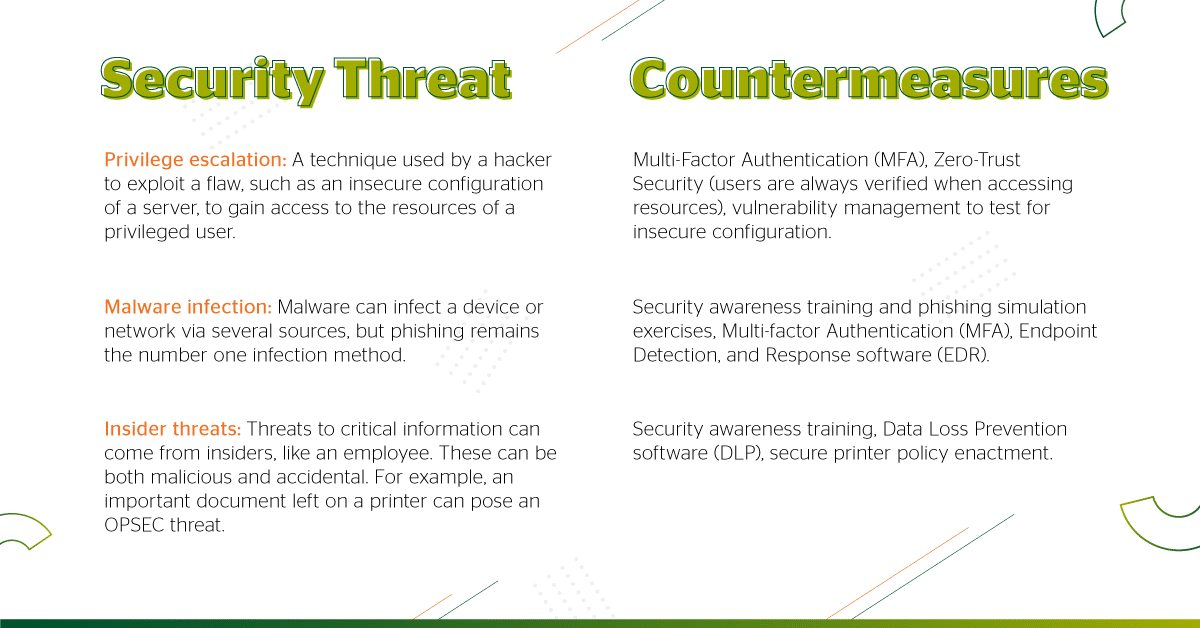
Privilege escalation: A technique used by a hacker to exploit a flaw, such as an insecure configuration of a server, to gain access to the resources of a privileged user.
Countermeasures: Multi-Factor Authentication (MFA), Zero-Trust Security (users are always verified when accessing resources), vulnerability management to test for insecure configuration.
Malware infection: Malware can infect a device or network via several sources, but phishing remains the number one infection method.
Countermeasures: Security awareness training and phishing simulation exercises, Multi-factor Authentication (MFA), Endpoint Detection, and Response software (EDR).
Insider threats: Threats to critical information can come from insiders, like an employee. These can be both malicious and accidental. For example, an important document left on a printer can pose an OPSEC threat.
Countermeasures: Security awareness training, Data Loss Prevention software (DLP), secure printer policy enactment.
Operations Security Jobs
Operations Security (OPSEC) is a multidisciplinary area of cybersecurity. Typical roles in OPSEC include:
Operations Security Analyst: Understands the application of cybersecurity measures, locates vulnerabilities, identifies, and implements security measures. These roles typically work collaboratively with other security teams.
Security Operations Manager: Develops OPSEC programs that focus on core areas, e.g., insider threats. Develops OPSEC plans and analyzes the OPSEC environment. These roles typically collaborate with team members and other key management.
Operations Director/Head of Operations Security: Oversees the entire OPSEC program, manages the budget, and communicates with the board on security matters.
Working in OPSEC can be a very fulfilling career. Security analysts are like modern-day cyber-sleuths, responsible for understanding threats and countermeasures. Vulnerability hunting is often a task that requires curiosity, diligence, and a high degree of technical knowledge and competence. Management roles in OPSEC offer a way to manage OPSEC programs and deliver effective cybersecurity protection.
Typically, a career in OPSEC involves gaining experience or certifications in specific areas such as computer security. Many roles in Operations Security require excellent writing and communication skills.
The Future of Operations Security
Cybersecurity is rarely out of the news with some of the world’s largest brands becoming victims of cybercrime. The cybercriminals behind those crimes are cunning adversaries who require intelligent cybersecurity professionals to mitigate their activities. Cybersecurity is an exciting area to work in, and Operations Security (OPSEC) is at the core of the discipline. With cybercriminals continuously working to avoid security measures, a career in OPSEC will always be exciting and challenging. As an OPSEC professional, you need to think like a hacker and know their motives and methods.
Are you ready to start your cyber career? Gain knowledge of operations security and learn what it takes to ace the certification exams with the University of Miami Cybersecurity Professional Bootcamp. Fill out the form below to schedule your call with our admissions team or call us directly at (305) 425-1151. Your future is one call away.



