The Internet is like a sea and it’s important for people to learn how to navigate the murky waters of connectivity and privacy. As smartphones, computers, and laptops become even more pervasive, the odds of falling prey to a cyberattack are high. With constant use of E-commerce websites and apps, email, social media accounts, banking apps, dating apps, etc., the list of vulnerabilities is ever-rising.
Cyber threats have always been around. Still, the rise in the percentage of the people connected to the Internet during the COVID-19 pandemic has given attackers more chances to take advantage of the circumstances and hack both companies and individuals.
According to the UNICRI 2020 report, in January, Google listed 149k live phishing and malicious websites. That figure increased in February to nearly 293k. In March, that figure had risen to 522k – a 350% rise since January. According to Cybersecurity Ventures’ 2019 Official Annual Cybercrime Report, cybercrime will cost the world $6 trillion yearly by 2021.
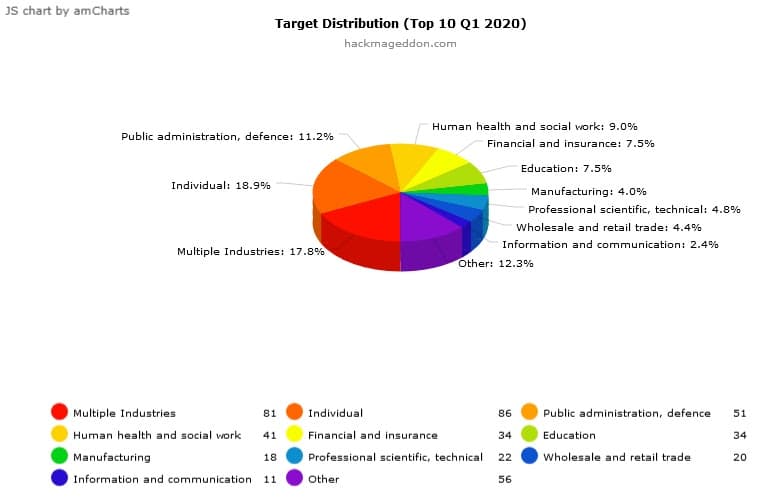
The following image shows that individuals are still the favorite targets for hackers, according to the Target Distribution Chart.
Today, it is crucial to follow the best cybersecurity practices at work and at home, since many people are now working remotely due to the COVID-19 pandemic. Read on to learn how to keep your online presence secure.
Prevent Cyber Attacks Online with These Tips
Internet security is essential for everyone. Here are eight simple steps to keep devices safe and personal data secure.
Install the Latest Software and Applications: Hackers regularly use vulnerabilities in software and apps to infiltrate computers and smartphones to seize your identity, financial data, or card details.
Software or app updates fix the vulnerabilities and install them to keep all the devices secure. You’ll usually receive a notification on your laptop or smartphone to notify you that a software update is available to be installed. Do not ignore this message.
Use a Strong Password: Attackers can use your email address to obtain your private data, such as bank account information, home address or birthdate. It is always essential to use a complex and unique password for your email because if attackers seize the password for one of your less valuable accounts, they can’t utilize it to gain your main email account.
Use Updated Browsers and Plugins: Hackers also use vulnerabilities in web browsers to steal information, and that is why the companies always release periodic updates to repair vulnerabilities. Installing the most advanced versions makes the device safe. The third-party plugins also contain many severe vulnerabilities. It is, therefore, necessary to regularly use updated plugins.
Use VirusTotal: Never click any suspicious links or PDFs. Hackers try to use malicious links or PDFs to install malware on your computer. Always scan PDF files and links with VirusTotal. It uses antivirus scanners and domain blacklisting services to inspect and validate links and files. Any user can upload a file from the device using their browser and send it to VirusTotal to detect malicious content.
Allow “do not track” in the browser: Many browsers contain a “do not track” option for websites that try to collect or track your browsing data. Still, what follows depends on the website only – but most sites don’t alter their function and seem to overlook the call. Still, it is always a good habit to enable the “do not track option.”
Use a VPN or Tor Browser: Virtual proxy networks or VPNs allow users to keep their privacy intact by encrypting the data. In VPNs, the encrypted data is transferred to the VPN server. After this, the VPN decrypts the data before forwarding it to the destination.
This process doesn’t allow internet service providers to track you. Users can also use the Tor browser. Tor is not exactly a VPN, but it is special because it is an open-source browser that allows anonymous communication with a network of specially built servers.
Check HTTPS: HTTPS secures your connection from your device to the visiting websites. These days most websites are HTTPS-enabled and show a green or gray lock in the address bar. HTTPS makes it difficult for anyone to see your internet traffic to steal your information.
Use a Firewall and a Password Manager: Always use an antivirus and firewall security software on your device and update it periodically no matter how thoughtfully and carefully you use the internet. Threats can be planted even in the most prominent websites; therefore, it is important to use a good antivirus program. Also, never use the same password everywhere.
The volume of data and password breaches that happen when websites are hacked makes it very vulnerable to use the same password again everywhere. However, memorizing robust passwords for all those many websites is difficult and leaving sticky notes with complex passwords is just as harmful as using a weak password. In such cases, a password manager plays an important role. They encrypt and save your login credentials for any website and allow you to log in automatically.
With a password manager, you only have to remember the one master password.
Secure Your Social Media Usage

The most popular social media platforms like Twitter, Facebook, Instagram have billions of users. Hackers can use these social media platforms to gather information (Reconnaissance or Footprinting) of a potential victim. Therefore, it is essential for you to secure your social media usage, as well. Here’s how:
- Create a different email for social media accounts. If you are hacked, then hackers won’t be able to get other valuable information.
- Use two-factor authentication. This is an extremely reliable way to secure your social accounts from illegal access.
- Delete unused accounts. It is always good to delete unused accounts, especially when uninstalling the app from your phone.
- Don’t use third-party apps. Only allow legal applications and be sure you understand the policy of what you are allowing the particular app to access.
- Never trust internet strangers: Don’t accept friend requests from unknown people. There is no need to accept friend requests if you do not know someone. Hackers often create fake accounts for social engineering
Tips for Keeping Organizations Safe
Hackers sometimes target big organizations. Your organization may have various security policies and tools in place, but one small error from a single employee could lead to a significant data breach. The following are some of the important tips to keep your organization safe.
- Ignore pop-ups, unfamiliar emails, and links: Never disclose personal or company data to unknown emails. Pop-ups or malicious links can lead to a Phishing page and, ultimately, data theft. It’s also the method used by hackers to carry out ransomware attacks on the target.
- Invest in security: Smaller companies might linger on investing in a proper security system, but it is essential to avoid a data breach. This normally involves securities such as powerful antivirus and malware discovery, SIEM, SOC, and SOAR teams, tools and solutions, robust data back up policies, and running routine system checks.
Conclusion
Having the awareness and following the tips mentioned above can save you or your organization from attackers. Remember that one small error or just one click on a malicious link could lead to a cyberattack. Following these key cybersecurity tips could be the difference between a secure company or individual and an easy target.
Want to learn everything there is to know about cybersecurity in less than one year? Now you can with the University of Miami Cybersecurity Professional Bootcamp.
Get the hands-on training that prepares you for a successful career in cybersecurity, no experience or certification required. You bring the determination to make this world a better place, we’ll bring the expert guidance you need to make it happen.



