Social engineering is a type of cybersecurity attack that uses deception and manipulation to convince unsuspecting users to reveal confidential information about themselves (e.g., social account credentials, personal information, banking credentials, credit card details, etc.). Social engineering can occur over the phone, through direct contact, or via the Internet. And may target an individual or the company where they work.
Many SE attacks aim to deceive a victim into installing malicious software on their device to gain full control over the targeted computer and to use it to spread the infection to other places within the network.
Adversaries find it easier to exploit human errors than to exploit system and software vulnerabilities to gain unauthorized access to the target system. Human errors make SE attacks more devastating to organizations as no one can predict human behavior against such attacks.
There are mainly two ways to deploy social engineering attacks. The first one relies on the Internet, with email being the most common avenue l, and the second uses the phone or in-person deception.
Nevertheless, many attackers utilize both types to gain useful insight into the target before launching an attack.
E-mail Phishing Attacks
A phishing email is a type of social engineering attack that uses online messaging to acquire sensitive information from a victim or install malware. This can be done via email, instant messaging, social media platforms, and apps, or text messages. These attacks commonly happen through email attachments and malicious links on their device.
To know how to mitigate phishing emails risks, we should first have an idea about the general format of such emails (see Figure 1).
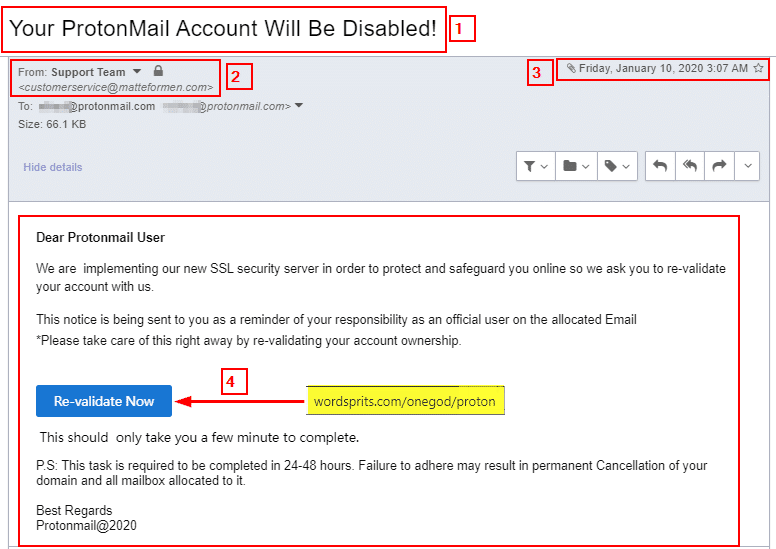
From Figure 1, we note the following:
Email subject: The subject uses aggressive or threatening language. Phishers usually use scare tactics to push the victim to act promptly without thinking. According to Barracuda Networks’ “Spear Phishing: Top Threats and Trends” report, the most used email phishing subjects are:
- Hello, Request, Follow up, Urgent/Important, Re:
- Are you available? /Are you at your desk?
- Payment Status, Purchase, Invoice Due, Direct Deposit, Expenses, and Payroll
Sender email: The sender uses an email address hosted on matteformen.com; however, the email is supposedly from the ProtonMail email provider. A mismatched address is a clear clue that this email is not from the pretended sender. We can also investigate the sender domain name to see whether it’s considered malicious. There are many free services to check whether a particular domain name is malicious:
- Norton Safe Web (https://safeweb.norton.com)
- IsItPhishing (https://isitphishing.org)
- Phishtank (https://www.phishtank.com)
- Virus Total (https://www.virustotal.com/#/home/url)
- AbuseIPDB (https://www.abuseipdb.com)
- Kaspersky VirusDesk (https://virusdesk.kaspersky.com)
Email date/time sent: Check the email sent time. If the email pretends to be from your company or bank, did they send it during official work hours? Check the date also, did they send it during the holidays?
Investigate email content: Hover your mouse over the email body’s hyperlink to reveal the correct address. For this example, the “Re-validate now” button should direct to ProtonMail.com; however, it leads to another domain name https://wordsprits.com/onegod/proton (see Figure 2).
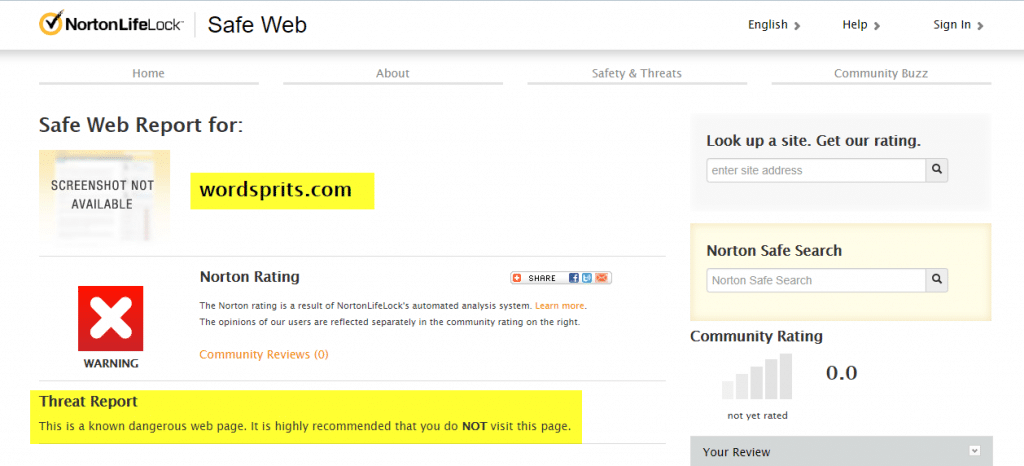
Now that we know the general format of phishing emails, let’s see some practical examples of how social engineering attacks work against individuals and corporations:
An individual’s confidential information can be acquired through impersonating a trusted entity, like a legitimate bank, to lure the victim into disclosing sensitive information. Usually, this can happen by clicking a link in the malicious email that takes the victim to a fake web page to enter/update personal information.
Once an attacker has this information, they can use it to blackmail the victim, make unauthorized purchases using stolen credentials, or use such information (e.g., employee login credentials) to launch an advanced attack against a target company. Attackers can also use the same phishing emails to install a keylogger, which records the keys you strike on your keyboard, on victim devices to steal sensitive information silently.
In an enterprise context, the losses can be more significant. For instance, most Advanced Persistent Threat (APT) attacks use phishing emails as an entry point to surpass all network security perimeters. By doing so, they can infect and propagate ransomware in a closed environment or gain unauthorized access to secure areas within the target network.
Social Engineering is Bad for Business
The vast technological development made the Internet the primary medium to launch SE attacks. However, other SE techniques are still used by criminals to retrieve sensitive information that could be used to attack an IT system.
- Shoulder surfing: In this type, an attacker gains access to sensitive information as users perform regular tasks. For example, an attacker may capture a user’s passwords using keylogging to watch them type them on the keyboard.
- Dumpster diving: In this type, an attacker tries to retrieve sensitive physical information from materials thrown in the trash. Many companies discard different kinds of papers without proper shredding (e.g., calendar meetings, user lists, system usage manuals). This unsecured practice is not limited to documents; for instance, some companies get rid of old computers without adequately destroying them or securely wiping data on the hard disk. An attacker can gain sensitive information by looking in the garbage or recovering from old computers’ hard drives.
- Role-playing: In this kind of attack, an attacker will impersonate other legitimate users (e.g., technical support staff at some company) and try to take sensitive information from users to gain illegal access to their accounts.
- Keyloggers/Trojan horses: This attack requires compromising victim devices to install monitoring software. For example, an attacker causes the user to install malicious software on their machine unknowingly, either through an email attachment or other freeware programs such as games or screensavers downloaded from the Internet). The installed application records everything the user types on the keyboard and sees on the screen and sends it back to its operator (the hacker). This allows attackers to spy on victim activities and acquire a variety of information to impersonate the victim or gain unauthorized access to their online accounts.
- Open-source intelligence (OSINT): This is an intelligence-gathering method where an attacker tries to collect information from publicly available sources about the target (whether it is an individual or an organization) and uses it to customize an attack. An example of OSINT gathering is using the wayback machine website to retrieve an old version of a web page.

Countermeasures Against Social Engineering Attacks
- Offer cybersecurity awareness training programs for your employees to recognize phishing emails and understand the security risks associated with them.
- Do not send any personal or sensitive work information via email systems, especially your account credentials.
- When you are in doubt, do not click any link in the received email and investigate the links mentioned before.
- Access your webmail over a secure connection (SSL certificate) only.
- Do not access your email account using free, open Wi-Fi access points in public places, but if you must, for whatever reason, use a VPN service.
- Do not reply to spam emails. Delete them permanently.
- Be extremely cautious about email attachments and do not open attachments from unknown senders.
- Disable HTML in your email client to prevent executing any code in the received emails. Major popular email clients like Thunderbird and Outlook disable them by default.
- Do not publish your primary or personal email online.
- Use strong, complex passwords to protect your email account and consider using two-factor authentication when possible.
- Do not use a free email service (e.g., Gmail. Hotmail) for mission-critical tasks.
Strengthen the Weakest Link
There are different types of social engineering (SE) attacks, trying to gain unauthorized access by exploiting the “human factor.” While this remains the weakest element in any cybersecurity defense plan, educating users about SE risks is still the best countermeasure technique against such attacks.
Now, more than ever, getting educated on current cybersecurity applications is not only crucial, it’s as easy as registering for our Cybersecurity Professional Bootcamp. Whether you’re an experienced IT professional or curious about a cybersecurity career, our admissions advisors are ready to help you take the first step to immersive, hands-on learning. Schedule your free consultation today!



