The enormous technological advancement in today’s information age has brought with it a tremendous increase in cybercrimes. There are already many types of cyberattacks, each with varying damage effects; however, ransomware attacks are still considered the most harmful.
Cybersecurity Venture has published many frightening predictions about global damage of ransomware attacks.
The first one predicts that global ransomware damage costs will reach $20 billion (USD) by 2021, the second expects a ransomware attack to hit a business every 11 seconds by the end of 2021.
Ransomware (also referred to as digital extortion) is a type of cyberattack that works by preventing a victim from accessing their computing device data using various methods. No one is immune to ransomware attacks as recent incidents show that individuals and both public and private organizations fall victim to this type of attack. Unfortunately, there is no sign that such threats will slow down.
While earlier versions of ransomware use simple techniques to lock the victim’s computing devices, modern variations employ encryption to lock up files. Encryption has become prevalent due to modern ransomware techniques making files impossible to recover without the associated decryption key.
Brief History
The ransomware threat has existed since the early days of computers. Its first documented usage took place in 1989 and was called AIDS Trojan.
The adversary, a biologist named Joseph Popp, sent 20,000 infected floppy disks labeled “AIDS information – Introductory Diskettes” via mail to the attendees of the World Health Organization’s AIDS Conference. The disks contained an interactive questionnaire used to trigger the malware after approximately 90 reboots of the victim’s machine.
The AIDS Trojan ransomware made the victims’ Windows operating system unusable by hiding all directories and restricting files on their computer’s hard drive. To lift the restriction, the victim had to pay $189 to a Panamanian post-office box.
Ransomware Types
The two main types of ransomware are crypto and locker ransomware.
Locker Ransomware is a simple form of ransomware. It works by preventing victims from accessing their files (e.g., locking desktop or login screen) and then demanding a ransom to revoke the restriction.
Crypto Ransomware is what most people think of when mentioning ransomware. It encrypts personal data on the targeted device until the victim pays the ransom and obtains the decryption key from the attacker. Some variants of crypto-ransomware will progressively delete files or release them to the public when that ransom is not paid on time.
Most modern ransomware families, which are variations of ransomware, are based on crypto-ransomware. Recent incidents worldwide have shown the devastating effects crypto-ransomware can have on individuals and organizations.
One of these incidents was the 2018 attack on the City of Atlanta, Georgia. According to the Atlanta Journal-Constitution, the recovery costs from the SamSam ransomware that hit Atlanta exceeded $17 million. This number is gigantic compared to the ransom payment, which was worth $50,000 Bitcoin.
How Does Ransomware Work?
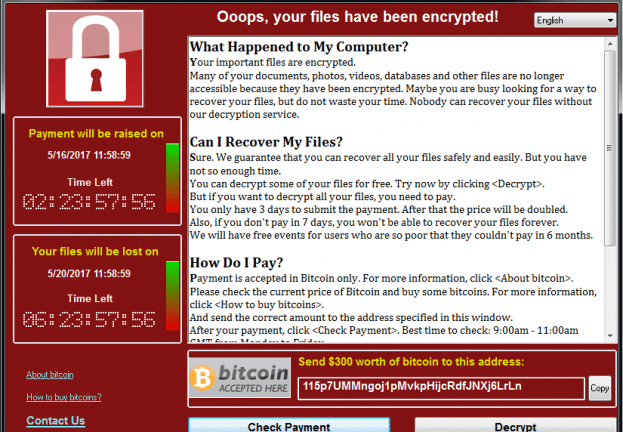
After the crypto-ransomware is installed, it will search for essential files based on their extensions and encrypt them; the ransomware will search for files on the local hard drive and all the attached external drives and network shares. After successfully encrypting all files, the ransomware will display a ransom note on the victim’s computer screen, as shown in Figure 1.
It will show a countdown timer and demand payment (ransom) to regain access to hostage files. Modern crypto-ransomware requests payment mostly via the Bitcoin cryptocurrency because it is almost impossible to track such payments.
What Distinguishes Ransomware From Other Malware Types?
Ransomware is a type of malware; however, many characteristics distinguish it from other malware.
- Each type of malware specializes in conducting a specific malicious action. For example, some malware steals user’s credentials, while other types spy on user activities (e.g., tracking user internet browsing history).
- On the other hand, ransomware focuses on locking a victim’s files to extort money without touching the underlying operating system files.
- While most malware types require administrative privilege to run, ransomware executes using the current privilege of the victim’s device.
- Crypto ransomware encrypts all file types by scrambling file names, making victims unaware of the actual number of files encrypted.
- Ransomware requests payments via anonymous payment methods, commonly via cryptocurrencies.
- Ransomware uses unique evasion techniques to surpass security solutions like antivirus software and firewalls.
- Ransomware has self-propagation capability in both internal and external networks (e.g., internet). Self-propagation means that the malware spreads without human intervention.
- In addition to encrypting files, some ransomware variants steal user credentials (username and passwords) and send them to its operators to blackmail victims.
- Many ransomware types are location-aware, meaning they only target users in specific geographic locations. For example, some ransomware families target users living in wealthy countries and discard users in impoverished states because they cannot pay the ransom.
6 Ways to Identify Ransomware on Your Device
Different symptoms distinguish ransomware infection from other malware. These tips will help you identify if you’ve become a victim of ransomware.
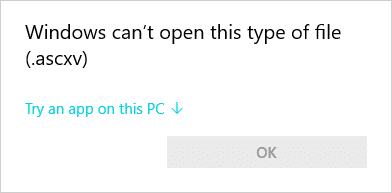
- 1. You cannot open your files. Whenever you try to open a file, your operating system displays a message stating that this file type is unknown (see Figure 2).
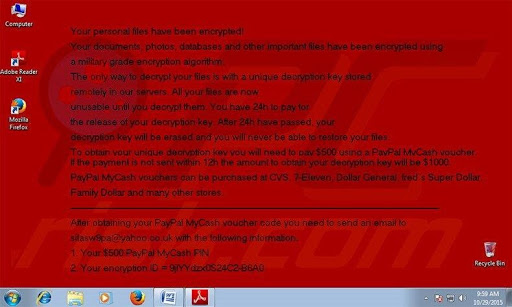
- 2. Some ransomware families may change your desktop wallpaper and replace it with the ransomware note (see Figure 3).
- 3. Your computer is locked, you cannot access your desktop or login screen, and a ransom note replaced your background image.
- 4. Some ransom notes appear as a program window that the user cannot close, without covering the whole screen. The note displays a countdown timer showing the remaining time before increasing the ransom, or the data is lost forever.
- 5. You see instruction files in all folders that contain encrypted files with instructions to guide the victim when paying the ransom.
- 6. Your file names are scrambled and have a different extension or no extension at all.
Ransomware Distribution Methods
There are various attack methods employed by ransomware operators to invade computer systems and networks. These are the go-to methods:
Email services. Email is still the primary medium for spreading ransomware. Phishing and spam emails are considered the favored vehicle for distributing ransomware on a mass scale.
Malvertising. Malicious actors abuse legal advertisement channels (e.g., Google Adsense) to spread ransomware. Malicious code in the advertisements directs visitors to malicious websites housing ransomware.
Exploit kits. Attackers direct victims to malicious websites hosting exploit kits using a variety of methods. When the victim reaches the compromised site, an exploit kit will scan the victim’s device for vulnerabilities and tries to convince them to install ransomware or other malware.
Removable media. Infected USB devices are still widely utilized by cybercriminals to spread ransomware.
Office Macros. Malicious MS office documents downloaded from the internet can be exploited by criminals to download and install ransomware on the victim’s machine.
Pirated software may contain hidden malware that installs undetected when executing the installer.
How to Prevent Ransomware
There are various countermeasures to mitigate and stop ransomware. Here are some essential steps you can start taking now:
- Install antivirus and antimalware solutions.
- Install firewalls and Intrusion Detection Systems on the network perimeter.
- Keep your operating system and installed applications up to date.
- Use virtualization technology (e.g., Virtual Box) to prevent ransomware from infecting your system. You can use this virtual environment to open or execute email attachments and files downloaded from the internet without compromising your device.
- Do not plug untrusted USB devices into your home or work computer.
- The best way to prevent ransomware and other malware attacks is to have a security awareness program.
With more and more ransomware attacks being reported all over the world, the best method to stop this type of attack is to have the necessary security solutions installed on the endpoint and network devices in addition to having adequate cybersecurity awareness training.
Start Your Career in Cybersecurity
Become a part of the solution when you join the growing network of cybersecurity professionals. The University of Miami Cybersecurity Bootcamp prepares individuals like you for a lucrative and rewarding career in less than a year.
Our virtual, hands-on courses are led by experts who know exactly what organizations need to protect against cybercrimes like ransomware. The world needs more heroes on our side. Our team of Admissions Advisors is waiting for you. Fill out the form below to schedule your free consultation today.



